AWS S3
To keep your delivery pipeline secured, we are setting up dedicated permissions for CI (write-only) and CD (read-only).
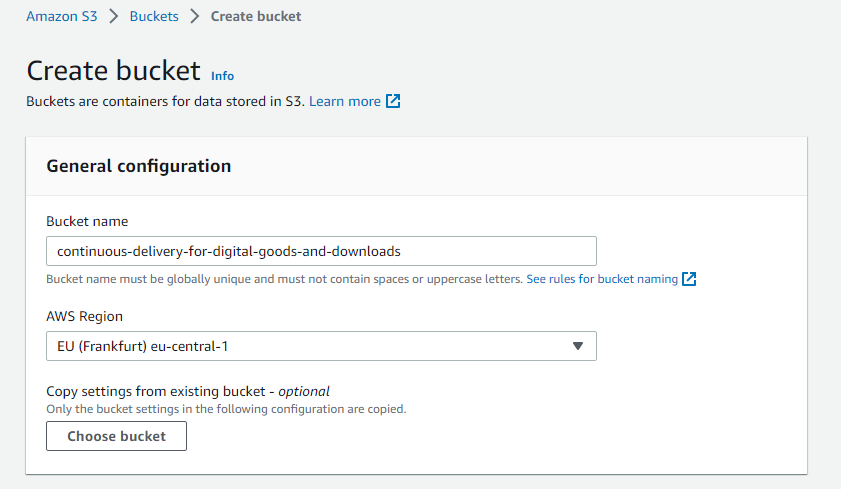
- Create a new bucket (
${BUCKET}) in AWS (__Amazon S3 > Buckets > Create Bucket). Note down the region (${AWS_REGION}).
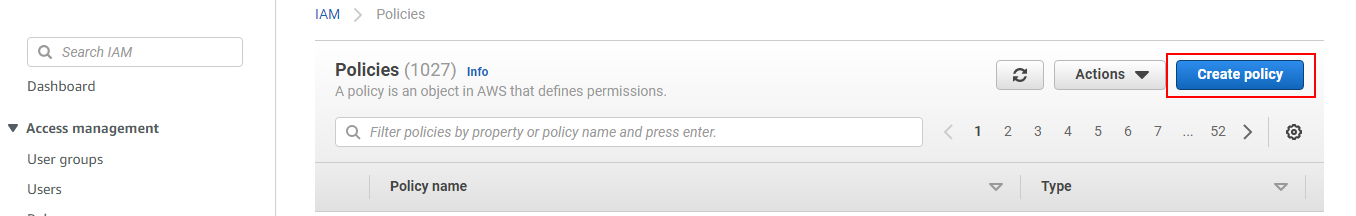
In AWS, go to IAM > Policies and use the button Create policy
Now create two new policies:
A write-only policy used in your CI environment (
${IAM_POLICY_WRITE_ONLY}) with the following JSON statement:{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": [
"arn:aws:s3:::${BUCKET}/*"
]
}
]
}A read-only policy used in WordPress (
${IAM_POLICY_READ_ONLY}) with the following JSON statement:{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": [
"arn:aws:s3:::${BUCKET}/*"
]
}
]
}
Go to IAM > Users and create two new users with __programmatic access.:
- Create a user for your CI environment
${AWS_CI_USER_WRITE_ONLY}. Attach the recently created IAM policy${IAM_POLICY_WRITE_ONLY}policy to it.
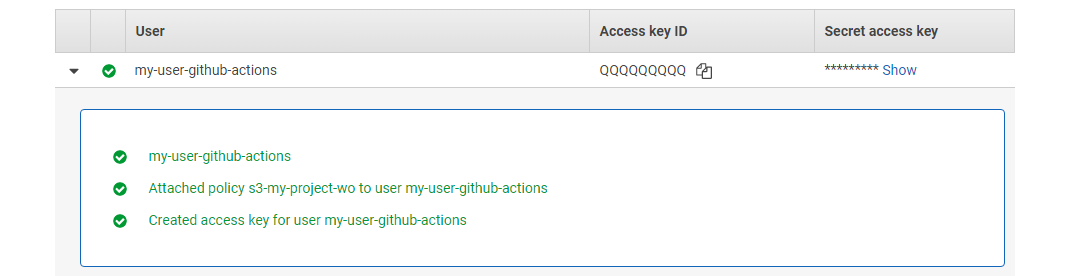
Note down the Access key ID (
${AWS_CI_ACCESS_KEY}) and Secret access key (${AWS_CI_SECRET_ACCESS_KEY}).- Create a user for WordPress
${AWS_WORDPRESS_USER_READ_ONLY}. Attach the recently created IAM policy${IAM_POLICY_READ_ONLY}to it.
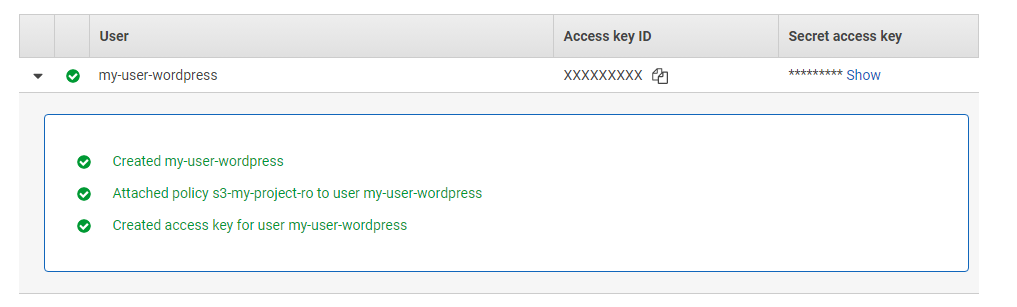
Note down the Access key ID (
${AWS_WORDPRESS_ACCESS_KEY}) and Secret access key(${AWS_WORDPRESS_SECRET_ACCESS_KEY}).- Create a user for your CI environment